The Digital Operational Resilience Act (DORA) aims to ensure financial and operational resilience for individual businesses as well as ensure economic stability for the European Union (EU) as a whole. The ability to be compliant and mitigate the impact of disruption through a robust incident management strategy begins with understanding the most critical business functions that comprise your organization. From there, you can accurately understand not only any potential impacts but also how to manage an incident end-to-end from disruption to recovery.
What is a Critical or Important Business Function?
Critical or important business functions are material to the operative and financial soundness of your organization and, on a systemic level, are relevant to the economic and financial stability of the EU. There are both internal and external considerations that must be kept top of mind when determining what is critical to your business; you must understand potential impacts not only on your own organization but also on the greater economic market.
First, a business function is considered critical based on the disruption it would have on your organization’s financial performance. This can be determined through financial impact analyses as well as risk quantification. You’ll also be able to determine which functions are critical by understanding the impact that each has on your ability to deliver products or services to your customers. To do this, you must perform business impact analyses (BIAs) and define your impact tolerances.
When defining your important or critical business functions, you also must take into account an external view. Ask yourself: what would be the impact on the greater market should one of my critical business functions experience disruption? Consider the size and type of customers that would be affected as well as time criticality. Ultimately, no matter your maturity level, incidents such as cyber risks can never fully be ruled out. Identifying and understanding the functions that keep your organization sound is key to minimizing the impact of any disruption.
5 Steps to Identify Critical Business Functions for an Agile DORA Strategy
When it comes to identifying important or critical business functions, the conversation is, unfortunately, usually very high level and focuses more on operationalizing over identifying and defining. We recommend following the below five steps to ensure a proactive and agile DORA strategy:
-
Identify: Critical Business Function Assets
First, you’ll need to determine functions across your entire information domain. This goes beyond just identifying services; it is crucial to map all dependencies stemming to and from your business functions to truly get an end-to-end perspective of your organization. Make sure to identify all assets associated with your critical business functions, including:
- People
- Processes
- Information
- ICT (information and communication technology) systems
-
Protect and Prevent: Best Practices and Internal Policies
The next step is to put policies in place that will ensure the resiliency of your ICT systems. This will require an understanding of certain ICT best practices that touch on both technical capabilities as well as building a culture of security and awareness within your company. For example, not only should you have robust cybersecurity measures and practices, but you should also work to ensure cybersecurity awareness and training across the company so that each individual plays a part in minimizing your vulnerabilities to cyber threats.
-
Threat Detection: Regular Testing of Critical Systems
Once the appropriate prevention practices are in place, you can then ensure that all threat detection measures are established to find and address relevant types of attacks, such as:
- Phishing campaigns
- Malware
- Ransomware
- Insider threats
- And others
As always, you’ll want to ensure detection and mitigation measures are clearly communicated to appropriate personnel. Regular testing of all critical systems is also necessary to ensure that they’re working appropriately. It is no longer sufficient to have testing be a check-the-box, once-in-awhile activity; you must develop a robust testing program that identifies vulnerabilities in your critical business functions and allows you to mitigate them before they happen.
-
Respond: Strategic Incident Management Processes
You will also need to have a strategic incident management process in place. This includes developing a consistent and effective approach that enables you to:
- Quickly address potential and real threats
- Keep your team informed and record communication
- Know exactly how to mitigate an issue to your critical business function before it occurs
- Analyze and learn from every incident
Just like with threat detection, you’ll need to regularly test your incident management processes, not only to ensure that your personnel are always prepared but also to identify any gaps or opportunities for improvement.
-
Recover: Strategies to Minimize Downtime Disruption
In addition to optimizing your response time and procedures, you’ll need recovery strategies to minimize the impact of any downtime caused by a disruption. These will ensure your ability to deliver your critical business functions should an incident occur. These may include:
- Implementing data backups
- Establishing redundant capabilities
- Identifying alternative solutions and/or reducing concentration risk
- Creating alternative processes and workflows
Common Challenges with Identifying Critical Business Functions
In a recent webinar of ours, 36% of attendees reported that the biggest roadblock that they’ve faced with their DORA program has been siloed information across teams and departments. This, ultimately, results in siloed capabilities as well as inconsistent language and understanding of criticality. It is crucial that all teams work together and fully understand DORA’s requirements to determine critical functions along with their respective processes, resources, and measures that support delivery.
Another common challenge is misalignment across teams (38% reported this in our webinar) in regards to resilience capabilities. While many organizations already have resilience strategies in place, they are often not mapped to critical business functions. The solution here is to realign across teams to adopt a view that is business-function first. Consider each important business function and determine which capabilities support the delivery of that function (and how).
Overall, this is an opportunity to leverage the strategies that you already have in place and build them out into a holistic operational resilience framework. DORA necessitates that organizations across the EU share a common understanding of resilience; this applies internally to your organization as well.
The Importance of Incident Management within DORA
Incident management should encompass everything from the moment that an outage is detected all the way through to recovery: a complete end-to-end strategy. Incident management is a crucial component of DORA regulation because the guidelines set forth will ensure that major incidents are efficiently, accurately, and consistently reported to regulatory authorities. Doing so will also ensure that appropriate measures are taken in the case of an incident. In the effort to ensure economic stability in the EU, regulators must have a finger on the pulse on incidents that are occurring and have assurance that they are being resolved effectively and in a timely manner.
Previously, ESAs (European supervisory authorities) each had their own reporting requirements; one of the goals of DORA is to harmonize these requirements and impose a common classification methodology. DORA introduces a regulated way to identify, track, log, categorize, and classify any ICT-related incidents. Most organizations already have an incident management process in place so much of the reporting requirements will not be a huge adjustment for them. However, the new guidelines on classifying incidents will likely be the bigger change. In order to classify, you will need a thorough understanding of which of (and how) your critical business functions are affected, which emphasizes the importance of identifying these functions.
Communicating with Customers is Key to Compliance
DORA’s incident management regulation necessitates notifying customers who have been exposed to significant cyber threats and informing them of any protective measures that are available. This will require an intricate level of mapping that shows which of your important business functions are affected, which third parties and customers are impacted as a result, as well as any timelines associated with the incident. To achieve and maintain compliance, entities will need to have strategies for notifying their third parties and customers quickly and effectively while also maintaining reputation and trust.
Classifying Major Incidents Under New ITS/RTS Guidelines
In June 2023, the European supervisory authorities published new guidelines on classifying ICT-related incidents. Taking into consideration the criticality of impacted business functions, data loss, and other criteria, organizations now have a standardized methodology of classifying these incidents.
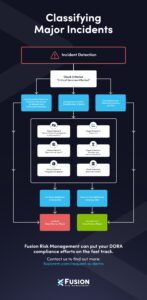
An important aspect to note is that the criteria focus more on the impact of the incident, not the source.
Incident Classification Primary Criteria Include:
- Clients, counterparts, and transactions – Who or what was impacted? What is the size, threshold, and percentage of your customer base that has been affected?
- Data loss – Was there any compromise in the integrity or availability of your data?
- Critical services – What, if any, was the impact on your services that you have identified as critical?
Depending on how many primary criteria you meet, your incident may already qualify as major. If you meet none of them, then the incident will not be considered major. If you only meet one primary criterium, your incident is still not major; however, it could be depending on whether you meet a certain number of secondary criteria.
Incident Classification Secondary Criteria Include:
- Reputational impact – While more qualitative, this criterium requires some perspective from management. This is a great example of how DORA is a cross-functional, all-hands-on-deck effort. Consider whether, for instance, the incident is in the news.
- Duration or service downtime – This criterium is still under discussion, as the criticality of the service will come into play.
- Geographic spread – How many member states are impacted?
- Economic impact – What are the direct and indirect costs associated with the outage?
If none or only one of the secondary criteria are met, the incident will not be classified as major. However, if you meet two or three secondary criteria after already meeting one primary criteria, it will be considered a major incident.
These classification guidelines are one example of the specific standards that will continue to be published throughout the DORA implementation window. Organizations that fall under the scope of DORA had until September 2023 to give feedback to regulatory authorities on guidelines. There is a conversation that entities are able to participate in and provide feedback on (which can be especially influential when given in groups) that has the potential to help shape the direction of DORA.
Understanding DORA Guidelines and Best Practices
As DORA regulation continues to be developed and communicated, it is crucial to be aware of new guidelines and best practices. Regardless of where you are in your DORA program, having a strong foundation and implementing a thorough, well-informed, and cross-functional approach will set your organization up for success as the January 2025 deadline approaches.
If you’re looking for a partner to help you not only achieve DORA compliance but also strengthen and develop your operational resilience program, Fusion is here to help! The Fusion Framework® System is the hub that unifies your entire DORA efforts in one place for implementation and optimization. Reach out to your Fusion Account Manager or request a demo to learn more today.






